Page 139 - Ellingham, Mark, Mariusz Meszka, Primož Moravec, Enes Pasalic, 2014. 2014 PhD Summer School in Discrete Mathematics. Koper: University of Primorska Press. Famnit Lectures, 3.
P. 139
s Pasalic: Symmetric Key Cryptography and its Relation to Graph Theory 127
plaintext ...
... ... ... S
SSS ...
... ... ... .
.
P .
... ...
...
... S
... ... ... ...
SSS ...
... ... ...
P
... ... ...
ciphertext
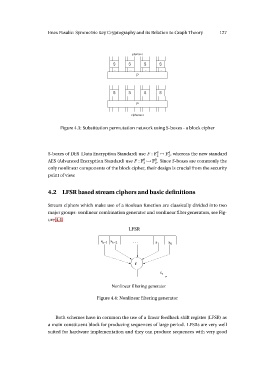
Figure 4.3: Substitution permutation network using S-boxes - a block cipher
S-boxes of DES (Data Encryption Standard) use F : 6 → 24, whereas the new standard
2
AES (Advanced Encryption Standard) use F : 8 → 28. Since S-boxes are commonly the
2
only nonlinear components of the block cipher, their design is crucial from the security
point of view.
4.2 LFSR based stream ciphers and basic definitions
Stream ciphers which make use of a Boolean function are classically divided into two
major groups: nonlinear combination generator and nonlinear filter generators, see Fig-
ure 4.4.
LFSR
sk−1 sk−2 ... s1 s0
f
zt
Nonlinear filtering generator
Figure 4.4: Nonlinear filtering generator
Both schemes have in common the use of a linear feedback shift register (LFSR) as
a main constituent block for producing sequences of large period. LFSRs are very well
suited for hardware implementation and they can produce sequences with very good
plaintext ...
... ... ... S
SSS ...
... ... ... .
.
P .
... ...
...
... S
... ... ... ...
SSS ...
... ... ...
P
... ... ...
ciphertext
Figure 4.3: Substitution permutation network using S-boxes - a block cipher
S-boxes of DES (Data Encryption Standard) use F : 6 → 24, whereas the new standard
2
AES (Advanced Encryption Standard) use F : 8 → 28. Since S-boxes are commonly the
2
only nonlinear components of the block cipher, their design is crucial from the security
point of view.
4.2 LFSR based stream ciphers and basic definitions
Stream ciphers which make use of a Boolean function are classically divided into two
major groups: nonlinear combination generator and nonlinear filter generators, see Fig-
ure 4.4.
LFSR
sk−1 sk−2 ... s1 s0
f
zt
Nonlinear filtering generator
Figure 4.4: Nonlinear filtering generator
Both schemes have in common the use of a linear feedback shift register (LFSR) as
a main constituent block for producing sequences of large period. LFSRs are very well
suited for hardware implementation and they can produce sequences with very good